There comes a time in the life of a software company when you decide to invest in cybersecurity.
And that’s good. This builds trust with users and prevents criminals from taking over your app, or worse - stealing your user's data. Just this alone could bring you hefty fines from data protection laws and harm your reputation in the market.
And there are two ways to find critical vulnerabilities: bug bounties programs and pentests. Both of them are effective in certain aspects, and both carry some drawbacks. Here we’ll put them side by side.
In this article you can expect to see:
- A breakdown of how bug bounty programs work and examples from the best programs.
- How you can get started with pentesting.
- A guide to help you choose the right solution to protect your business.
Let’s get started with Bug Bounty Programs
Bug bounty programs are initiatives that invite skilled ethical hackers to uncover vulnerabilities in an organization's systems and applications, providing rewards or bounties for their findings. These programs provide continuous testing, rapid risk identification, and rewards for uncovering vulnerabilities.
While bug bounty programs have limitations, partnering with platforms like HackerOne and Bugcrowd allows you to strengthen your organization's cybersecurity defenses.
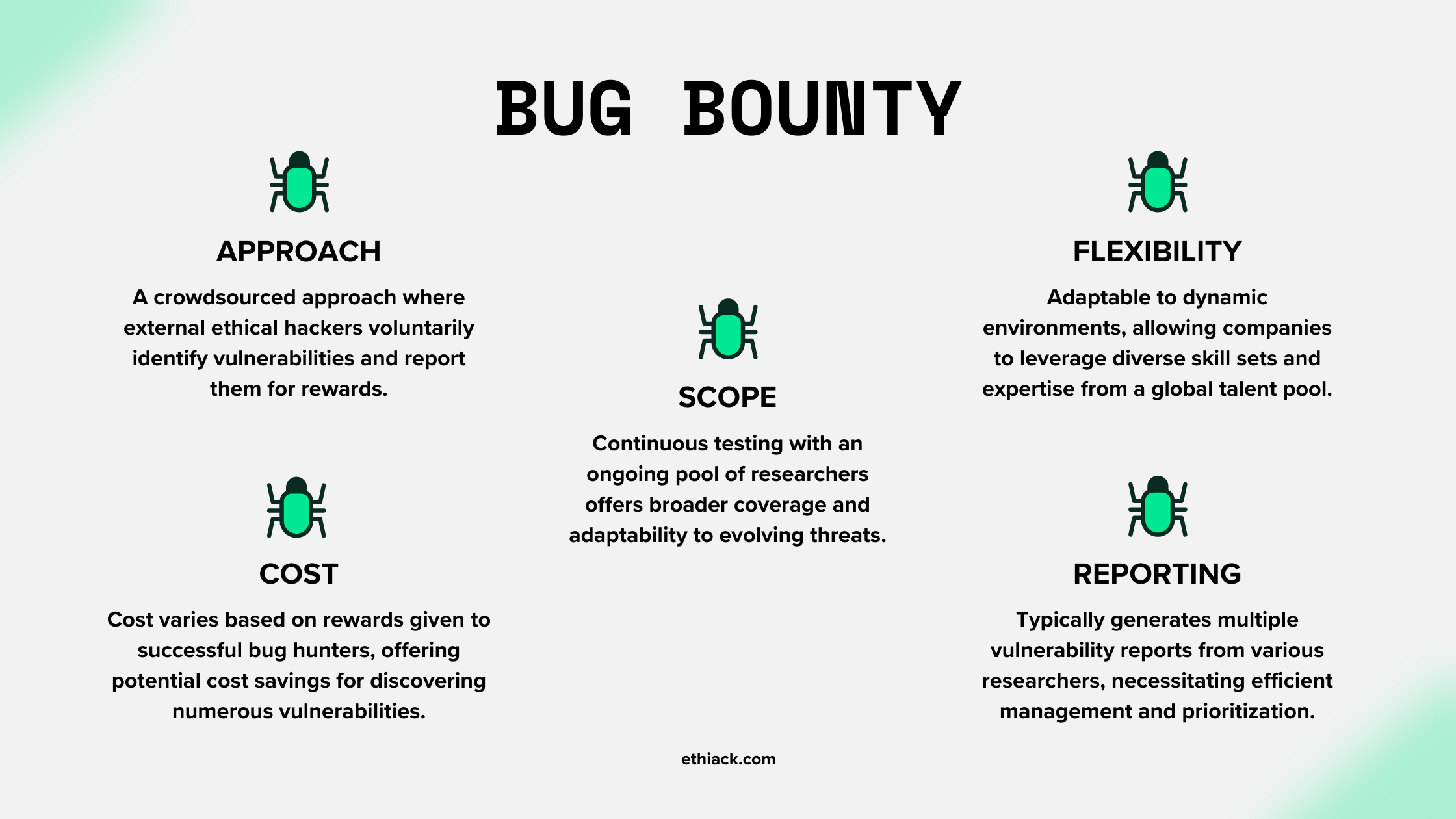
How to structure your Bug Bounty Program
Bug bounty programs invite external security researchers, also known as bug hunters, to discover and responsibly disclose vulnerabilities in a company's web applications. The programs typically involve the following steps:
- Define Your Scope: Take charge of your pentesting process by defining the scope of your assessment. Clearly outline the boundaries and objectives to ensure a focused and effective testing approach.
- Select Your Platform: Choose the most suitable platform to host and manage your bug bounty program. Consider factors such as reputation, features, and community engagement to make an informed decision. Popular platforms include HackerOne, Bugcrowd, and Synack, which provide infrastructure and coordination for the program.
- Set Guidelines and Rewards: You’ll have to establish clear guidelines for the ethical hackers participating, including rules of engagement, submission requirements, and expectations for responsible disclosure. The more enticing the reward, the more encouraged they’ll be to deliver fruitful submissions.
While the CVSS base score can serve as a reference, the bug bounty program rewards are based on severity, impact, risk assessment, and budget. Usually, the more critical the vulnerability is, the higher the payouts. The average rewards range from hundreds to thousands of dollars, depending on scope and severity. - Conduct Testing and Submit Findings: The ethical hackers then get to work and engage in testing the company's web applications within the defined scope. Once they discover vulnerabilities and submit detailed reports to the bug bounty platform, they’ll also include the steps to reproduce the issue and its potential impact.
- Validate and Remediate: Collaborate with your team to validate the identified vulnerabilities and prioritize remediation efforts and swiftly address the issues to enhance your organization's security posture.
- Reward and Recognize: The ethical hackers receive rewards for their valid and impactful submissions. The bug bounty platform facilitates the payment process, ensuring fair compensation for their efforts, and providing recognition for their valuable contributions to your cybersecurity ecosystem.
Several famous companies have successfully implemented bug bounty programs. Here are a few notable examples:
- Google: Google runs its Vulnerability Reward Program, offering big rewards for security vulnerabilities found in its web applications, Chrome browser, and Android operating system.
- Apple: Apple launched its bug bounty program in 2016, inviting researchers to report vulnerabilities in its operating systems, software, and services, with rewards reaching up to $1 million for critical issues.
- Microsoft: Microsoft's bug bounty program covers various products and services, including Windows, Azure, and Office 365. It offers rewards for vulnerabilities that can compromise user data or the company's infrastructure.
They’re good because they’re based on results
Bug bounty programs are great because you pay for results, not for hours. If bug hunters don’t find anything, or find only minor issues, then you won’t pay a dime. In addition, they’re also:
- Crowdsourced, which means you’ll tap into a global community of ethical hackers, with diverse range of skills and perspectives, instead of relying on one single pentester. This makes it easier to find vulnerabilities, as you’ll have more people working on it. And if one bug hunter can’t find the vulnerability, another with a different approach might be able to find it.
- Cost-effective, as you only pay for results (vulnerabilities found). This can be more cost-effective compared to pentesting, since organizations pay specifically for impactful issues that are discovered.
- Continuous, meaning security will be an on-going effort instead of one-time like with pentesting. Organizations benefit from ongoing vulnerability discovery and can proactively address issues, enhancing their security posture over time.
But these programs sacrifice process and detail
And while you do pay for results, the processes that they use to get to those results is out of your control. Common complaints usually revolve around the quality of the reports and the methods used to find the vulnerabilities.
- You lack control over scope and processes since every hacker has their own method. This can result in varying testing approaches and may lead to overlooking certain vulnerabilities.
- Reports can be very good… or very bad. You need to set criteria in the submission method to fix this since the reports submitted by ethical hackers can vary significantly in quality. That’s why it is crucial to establish clear submission criteria and guidelines to ensure actionable and accurate reports beforehand. This means it’ll take longer to get started with your bug bounty program, but it’ll save you effort down the line.
- It doesn’t go as deep as pentesting. Vulnerabilities requiring more time, effort, or just mental space will be put on the back burner. Sure, they’ll be rewarded more if they find them, but many bug hunters stray away from them. They may identify surface-level vulnerabilities but fail to find more complex or nuanced issues.
- It can end up being even more expensive, depending on the findings. This is somewhat bittersweet. You do want to find critical vulnerabilities - but if you find them, you’ll end up paying a heftier bill. But if you want the best hunters, you’ll have to offer big rewards.
Pentesting: good for depth but lacks frequency
Pentesting simulates real-world attacks to identify vulnerabilities in web applications. It usually, uncovers deeper vulnerabilities, but it's conducted less frequently.
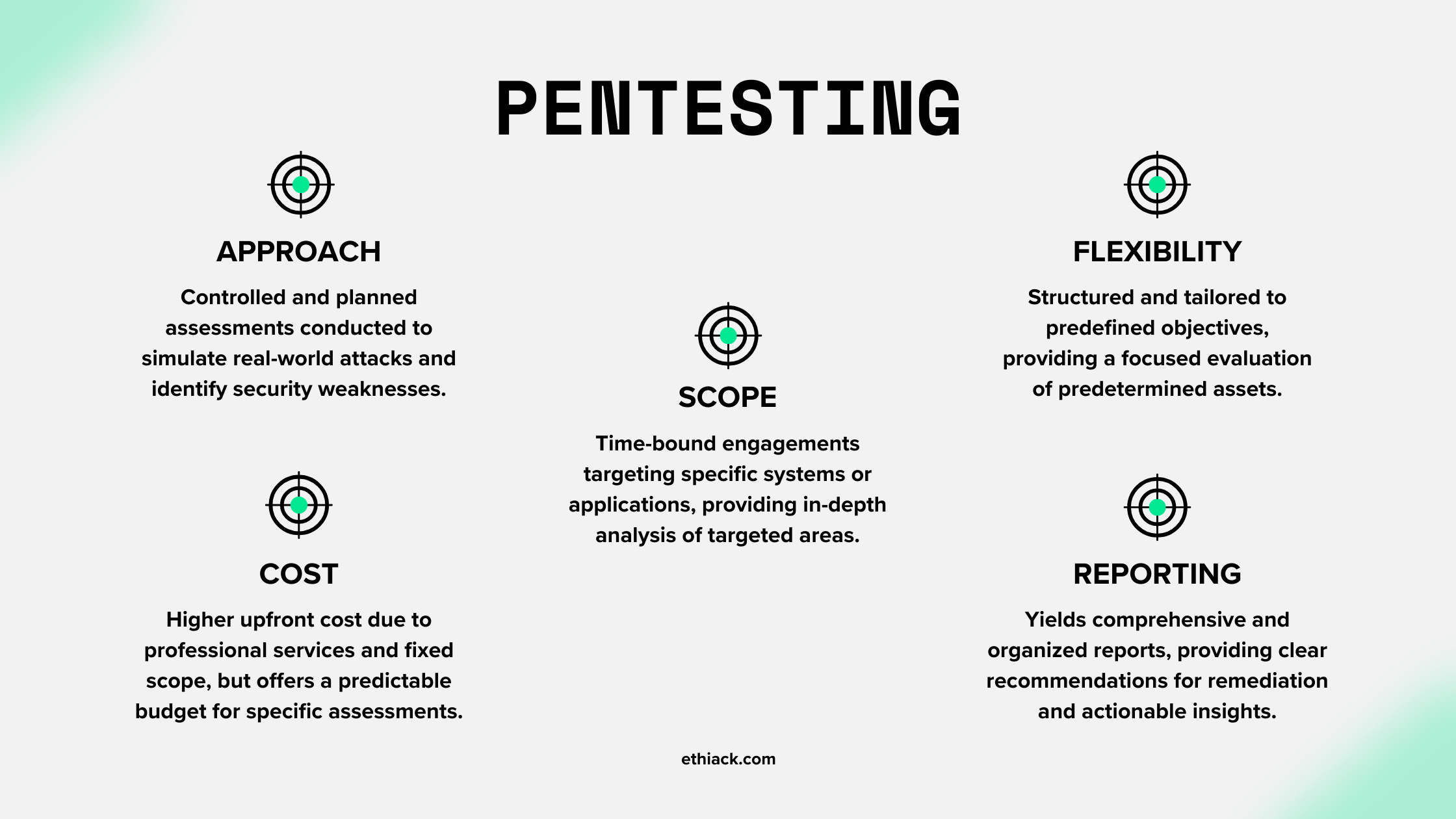
How to get started with pentesting
Pentesting typically follows these steps:
1. Planning and ScopingThis is an important aspect that will help decide the course of the pentest. Here’s how you should do it.
- Define goals: Clearly define the objectives of the pentesting engagement. For example, it could be to identify vulnerabilities in a specific web application or assess the overall security of a network infrastructure.
- Identify the scope: Determine the scope of the pentesting by identifying the target systems, applications, and networks that will be included in the assessment. This could involve specifying the IP ranges, URLs, or specific components that will be tested.
- Test the methodology selection: Choose the appropriate testing methods, tools, and techniques based on the scope and objectives. This could include techniques such as black box testing, white box testing, or gray box testing, as well as selecting specific tools or frameworks for vulnerability scanning or manual testing.
- Establish rules of engagement: Establish the rules of engagement that define the boundaries, limitations, and constraints of the pentesting. This could involve specifying the testing schedule, communication channels, and any specific rules or guidelines that need to be followed.
- Take into account legal and ethical considerations: Ensure that the pentesting activities adhere to legal and ethical guidelines. This involves obtaining proper authorization from the relevant stakeholders, ensuring compliance with privacy regulations, and respecting any restrictions or limitations set by your organization.
2. Information Gathering
Gather relevant information about the target environment, such as network architecture, application frameworks, and technologies in use. This helps in understanding potential vulnerabilities and attack vectors.
3. Vulnerability Assessment
Conduct a systematic analysis of the target systems, applications, and networks to identify known vulnerabilities. This may involve using automated tools, manual inspection, and testing for common vulnerabilities such as SQL injection, cross-site scripting (XSS), and insecure configurations.
4. Exploitation
Attempt to exploit the identified vulnerabilities to gain unauthorized access, escalate privileges, or manipulate the target systems. This step helps in validating the severity and impact of the vulnerabilities.
5. Reporting
Document the findings, including the identified vulnerabilities, their potential impact, and recommendations for remediation. Provide a clear and concise report that allows stakeholders to understand the risks and take necessary actions.
Different organizations may have variations in their pentesting processes, but common approaches include:
- Black Box Testing: You should pick Black Box Testing if you prefer that the testers rely solely on external reconnaissance and analysis, without any prior knowledge of the target systems. This approach allows for a realistic simulation of an external attacker.
- White Box Testing: the most complete approach. Here, the hacker has full knowledge of the target systems, including architecture, source code, and network configurations. This comprehensive understanding enables a thorough analysis of internal components and potential vulnerabilities.
- Gray Box Testing: You should pick Gray Box Testing if you prefer testers to have limited knowledge of the target systems, simulating an attacker with partial insider information. This approach strikes a balance between the realism of black box testing and the efficiency of white box testing.
.png)
Pentests go deeper into your assets
Pentests go beyond the surface, venturing deep into the intricate layers of your assets. They provide a comprehensive evaluation that uncovers vulnerabilities and potential business logic flaws, ensuring a thorough assessment of your security posture. With this in mind, pentests reveal the unseen, uncovering weaknesses that automated scanning alone cannot detect.
- You can take charge of the testing process since Pentesting offers greater control over the process at hand. Define the scope, set objectives, and choose testing methods that align with your needs. This is a tailored assessment that addresses your specific concerns.
- Allows you to unveil the full scope of your target systems by offering you a comprehensive evaluation. It goes beyond surface-level vulnerabilities and explores potential business logic flaws. Through this thorough examination, hidden vulnerabilities that automated scanning may miss are revealed.
- You can specifically direct your focus and efforts to specific areas of concern or critical assets and tailor your security assessments to align with your priorities and risk profiles. This targeted approach ensures that your resources are strategically deployed where they are most needed.
But pentests happen way too rarely
As we mentioned, the big drawback of pentests is that they happen way too rarely. It’s common for companies to do only one pentest per year, maybe two. On top of that, you have a few other disadvantages:
- Happens once per year VS the dozens of code deployments you have in a year since pentesting is typically conducted periodically, often once a year or on a scheduled basis. This doesn’t align with the faster pace of software development and deployment cycles, leaving potential vulnerabilities undiscovered until the next assessment.
- You rely on the expertise of individual testers, meaning that the effectiveness of pentesting heavily relies on the skills, experience, and knowledge of the pentesters you hire. You’ll have to ensure to engage highly skilled and reputable pentesting professionals or teams.
- Higher costs (which is not necessarily bad when security is at stake), especially when you engage with experienced and specialized pentesting professionals. However, the costs associated with pentesting can be justified by the potential risks and damages that can be mitigated through the identification and remediation of vulnerabilities.
- It’s mostly a checklist-based method, which can be a bit restrictive in terms of new ways to find vulnerabilities. This process employs previous predefined test cases and techniques to systematically evaluate the security of targeted assets. In this case, the checklist serves as a structured framework, guiding the pentesters to check specific security controls, configurations, and known vulnerabilities.
Ask yourself these questions before choosing between bug bounty or pentesting
When deciding between bug bounty programs and pentesting, there are several important factors to consider. Here's an elaboration on the questions you should ask yourself before making a choice:
1. How many resources can you dedicate to this this year?
An annual pentest will set you back around 4,000 USD if you’re a small and non-complex company, up to more than 10,000 USD depending on the size and complexity of the organization. A bug bounty program might be cheaper, but if you don’t spend enough money then you might be stuck with low-impact vulnerabilities.
For this, you’ll have to consider the size of your company, the scope and complexity you want, the number of assets, what’s your goal with this test, and the overall data sensitivity. Don’t forget that for this process you’ll also have to take into account your available budget, time, and personnel resources.
Bug bounty programs often require allocating resources to manage the program, review submissions, and coordinate with ethical hackers. Pentesting may involve engaging external pentesting providers or dedicating internal security resources.
Evaluate what resources you can realistically allocate to ensure the success of the chosen approach.
2. How many assets do you have?
Assess the number and diversity of assets within your organization.
If you have a large number of web applications, platforms, or assets that need testing, bug bounty programs can be highly effective. You can leverage the collective expertise of ethical hackers to uncover vulnerabilities across a broad scope. A rough estimate for a "large number" of assets in this context could be anywhere from 50 to several hundred or even thousands of assets.
However, if you have a limited number of critical assets or specific systems that require a more focused and in-depth assessment, pentesting may be the best choice. Pentesting allows skilled security professionals to simulate real-world attacks, providing valuable insights into the security posture of individual assets. A small number of assets could range from a handful to a few dozen. This could include critical systems, key web applications, or specific platforms that require thorough evaluation to identify vulnerabilities and potential business logic flaws.
If you want to discover immediately how many assets you have, check here.
3. How many processes do you have in place regarding security?
For this, you have to consider the maturity of your existing security processes.
If you already have robust security measures and a well-defined vulnerability management program, bug bounty programs can complement your existing practices. They provide an additional layer of continuous testing.
If your security processes are still evolving or need improvement, pentesting can provide a more structured and comprehensive assessment, helping you identify gaps and strengthen your security posture.
Ultimately, the choice between bug bounty programs and pentesting depends on your organization's specific circumstances, resources, and goals. It's often beneficial to combine both approaches, leveraging bug bounty programs for continuous testing and pentesting for in-depth assessments of critical systems.
An alternative way: the trifecta of cybersecurity
There is, however, a third way.
AI became the topic of the year, and now security experts started at ways to use AI to protect digital assets. This leads us to this third way: combining bug bounty programs. Pentesting, and artificial hacking. And it might very well be the best option on the table. Let’s see why:
- Artificial hacking runs 24/7 and finds common vulnerabilities to they get fixed immediately
Artificial hacking, often performed through automated vulnerability scanners and continuous monitoring systems, plays a crucial role in identifying common and known vulnerabilities. By running 24/7, artificial hacking can quickly detect and report vulnerabilities as they arise, allowing for immediate remediation.
This proactive approach ensures that common vulnerabilities are promptly fixed, reducing the overall attack surface of your web applications and systems. - Bug bounty programs allow hackers to find “superficial” and creative attack vectors, paid-for impact found
Bug bounty programs bring the power of crowdsourced testing by engaging ethical hackers worldwide. These programs incentivize hackers to discover vulnerabilities by offering rewards based on the impact and severity of the reported vulnerabilities. Bug bounty programs provide an additional layer of security assessment beyond automated tools and artificial hacking.
Ethical hackers can often find "superficial" or creative attack vectors that might not be easily detectable through automated scans. Their diverse perspectives and approaches can uncover vulnerabilities that may have been overlooked by traditional security measures. - Pentesting finds “deeper” creative attack vectors
This method goes beyond automated scanning and bug bounty programs. It involves a targeted and methodical approach to identify "deeper" and more sophisticated attack vectors.
Pentesters leverage their expertise to simulate real-world attacks, exploiting vulnerabilities and uncovering potential security weaknesses that may not be easily discoverable through other means. Pentesting provides a comprehensive evaluation of your systems and applications, offering valuable insights into your security posture and helping you prioritize remediation efforts.
The combination of these three components creates a powerful security trifecta.
➡️ Artificial Hacking provides continuous monitoring and quick identification of common vulnerabilities.
➡️ Bug Bounty Programs tap into the collective knowledge and creativity of ethical hackers to discover unique attack vectors.
➡️ Pentesting brings a structured and targeted assessment to uncover deeper vulnerabilities.
What do you get by implementing the trifecta of security
By implementing the trifecta of security, you can:
- Mitigate Common Vulnerabilities: Artificial hacking and bug bounty programs help identify and remediate common vulnerabilities promptly, reducing the risk of exploitation.
- Harness Collective Expertise: Bug bounty programs leverage the skills and creativity of a global community of ethical hackers, providing a diverse range of perspectives to identify unique attack vectors.
- Conduct In-Depth Assessments: Pentesting goes beyond automated scanning and explores more sophisticated attack vectors, uncovering hidden vulnerabilities and potential business logic flaws.
Remember that the trifecta of security requires careful planning, coordination, and resources. It is important to establish clear guidelines, set appropriate budgets, and establish effective communication channels with the ethical hacker community and pentesting providers.
Regularly assess and update your security strategy to stay ahead of emerging threats and maintain a strong cybersecurity posture!
Conclusion and next steps
When it comes to securing web applications, your organization can benefit from a combination of bug bounty programs, pentesting, and artificial hacking. Each component brings unique advantages to the table, creating a comprehensive and proactive security strategy.
With this in mind, here’s a recap for you:
Bug Bounty Programs
- Enables organizations to tap into the collective knowledge and creativity of ethical hackers.
- Discover unique and creative attack vectors.
- Provides continuous testing (depending on the program you implement).
- Incentivizes hackers to find vulnerabilities.
- Results in faster identification and remediation of potential risks.
Pentesting
- Offers a more structured and targeted approach.
- Skilled security professionals simulate real-world attacks.
- Uncovers deeper vulnerabilities and potential business logic flaws.
- Provides valuable insights into an organization's security posture.
- Helps to prioritize remediation efforts.
Artificial Hacking
- Involves continuous monitoring and automated vulnerability scanners.
- Detects common and known vulnerabilities.
- Runs 24/7 to promptly identify vulnerabilities.
- Reduces the attack surface and strengthens overall security.
Combining Bug Bounty Programs, Pentesting, and Artificial Hacking
- Achieves the trifecta of security (the best option)
- Mitigates common vulnerabilities
- Harnesses the collective expertise of ethical hackers
- Allows for in-depth assessments to uncover both known and hidden vulnerabilities
So, as some homework, here’s how you can get started:
1. Answer the questions we outlined above: How many resources do you have, how many assets do you have, and how many security processes have you implemented?
2. Based on your answers, pick one of the options. Or, alternatively, get started with Artificial Hacking, which carries the biggest ROI.
3. After 6 months, evaluate the impact of your strategy and adjust based on the results.
Remember that security is an ongoing process. Regularly reassess and update your security strategy, considering emerging threats, changes in your technology stack, and the evolving landscape of cybersecurity.
By taking immediate action and implementing the security trifecta, your organization can enhance its cybersecurity defenses, mitigate risks, and ensure the resilience of its web applications against potential threats.